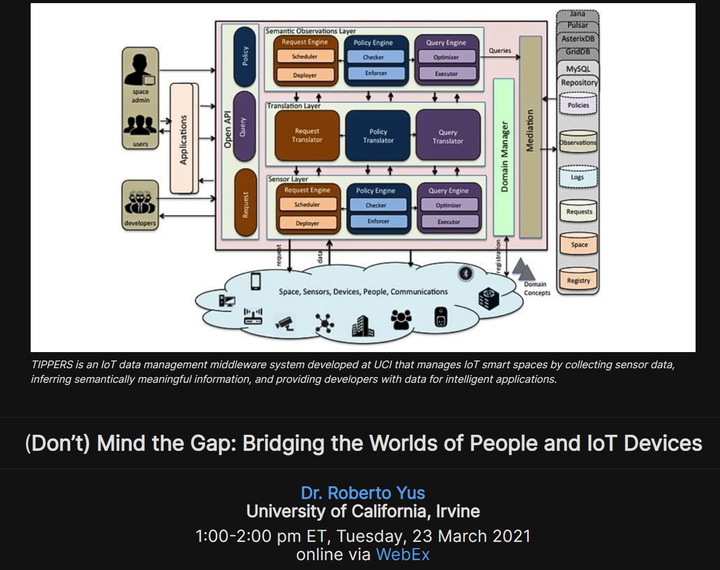
Abstract
The Internet of Things (IoT) has the potential to improve our lives through different services given the diversity of smart devices and their capabilities. For example, the IoT can empower services to make the re-opening of business during the current pandemic safer by monitoring adherence to regulations. But the large amounts of highly heterogeneous data captured by IoT devices typically require further processing to become useful information. The challenge is thus for IoT systems to determine which sensor data has to be captured/stored/processed/shared to, for instance, determine the occupancy of a specific office building or the spaces in which a potential exposure took place. This becomes even more challenging when IoT systems have to take into account privacy preferences of individuals such as the need to prevent sharing data about their daily patterns or habits. In this talk, I will discuss my efforts into helping IoT systems bridge the gap between the world of IoT devices and the world where people act. First, I will introduce a model to represent knowledge about sensors/actuators, people, spaces, events, and their relationships. Based on the model, I will explain an algorithmic solution to translate user requests and privacy preferences defined in a high-level more semantically meaningful way into operations on IoT devices and their captured data. Second, I will present a study on the practical privacy implications that such semantic data management operations have in the context of location data. Finally, I will overview my experience building and deploying an IoT data management system, TIPPERS, which has been deployed at UC Irvine and two US Navy vessels and is soon to be deployed in other campuses. I will conclude the talk discussing the exciting future work opportunities towards supporting the next generation of ubiquitous IoT data management systems and technologies that autonomously, transparently, and at scale, balance the trade-off between providing users with high utility and respecting people’s privacy requirements.